On Friday, a vulnerability called “Log4j” that effects a large variety of consumer and business applications was revealed. This threat effects a tool that many closed and open-source applications use for logging purposes. This vulnerability is rated at 10, which is the highest rating on the severity scale.
Software vendors around the world have been patching their applications to protect against this vulnerability and we have been working with our clients to ensure their apps are upgraded. An aggregated list of effected products can be found here: https://github.com/NCSC-NL/log4shell/tree/main/software#readme
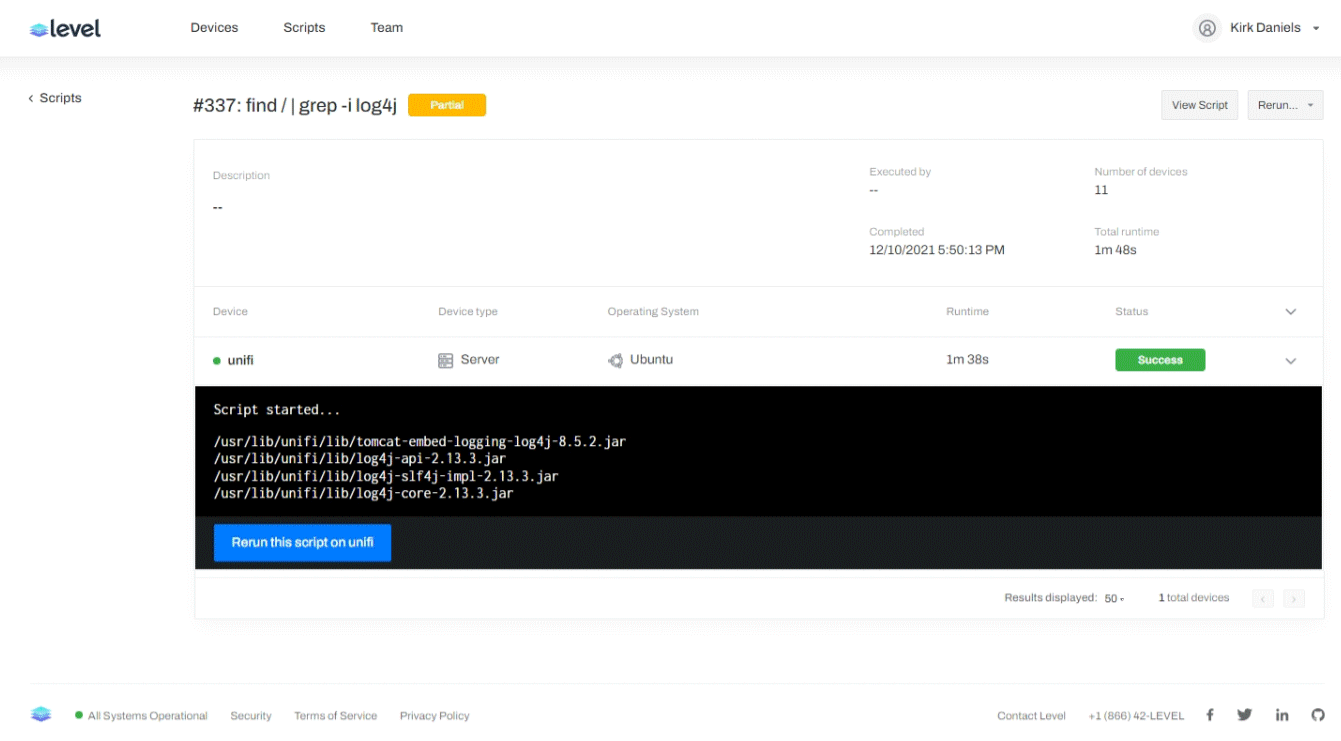
In addition to regular business applications, there are many IT infrastructure components that rely on the Log4j tools. Some notable examples are VMware vCenter, Cisco UCS Director, PaperCut, and Ubiquiti UniFi.
On Friday, before lists of effected products were aggregated, we used our remote management tool Level to scan our client machines for any trace of the Log4j tool. We discovered early on some products were using the Log4j tool and were vulnerable.
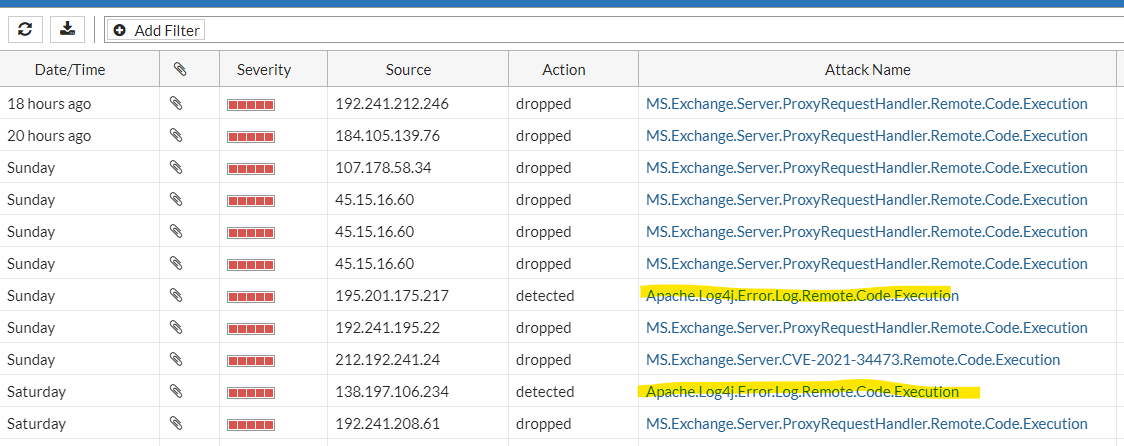
 Fortinet has released an Intrusion Prevention Service (IPS) signature that will detect if a hacker is attempting to leverage this vulnerability. Our clients with Fortigate firewalls will be additionally protected while we continue our push to ensure all vulnerable applications are being patched.
Fortinet has released an Intrusion Prevention Service (IPS) signature that will detect if a hacker is attempting to leverage this vulnerability. Our clients with Fortigate firewalls will be additionally protected while we continue our push to ensure all vulnerable applications are being patched.
We will continuing our work on discovery and remediation in order to keep our client safe and secure! Any notable updates to our efforts will be appended here.
Update 1:
Fortigate firewall logs are showing that malicious scans on client networks were detected as early as Saturday. This vulnerability was quickly weaponized, and hackers surely wanted to take advantage that the weekend might afford them. Thankfully our clients’ Fortigate IPS databases are setup to update automatically, so they received new IPS signature before the weekend began!