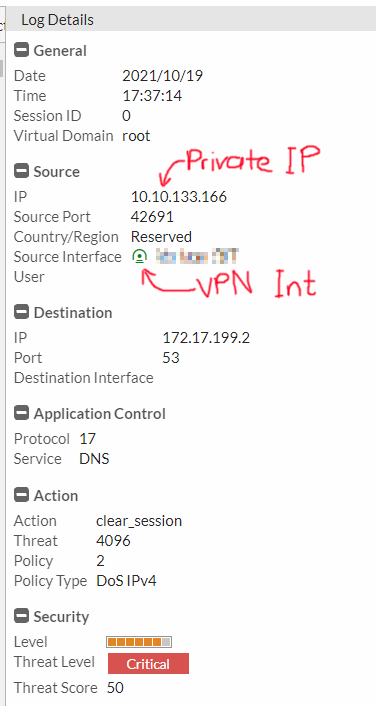
Applying a DoS policy on a WAN interface is a good practice that will help prevent flooding or abusive behavior from the internet. However, there is an undesired side-effect of choosing a WAN interface as the source for a DoS policy: If there are any VPN tunnels bound to the interface, then the VPN traffic is also inspected by the policy. This will result in the anomaly logs filled with private IP addresses with the VPN tunnel interfaces as the source — even though those interfaces are not selected in the DoS policy!
The first time I encountered this, I had assumed that we could negate private IP address ranges with “set srcaddr-negate“, but the negate feature is only available on regular firewall policies. After much trial and error we found a solution.
Solution:
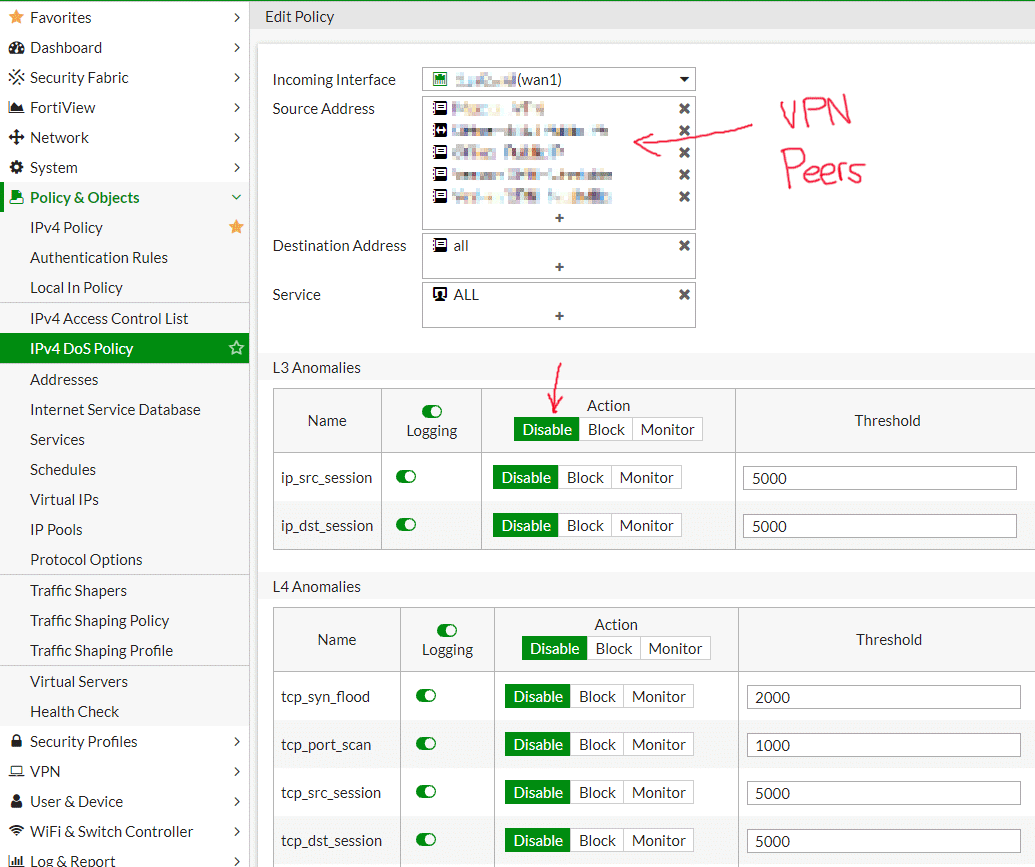
Create a second DoS policy and choose the same WAN interface. In the Source Address field, add all VPN peer IPs (public IPs) that are using that interface. Then set the action for all anomalies to Disable. Lastly, drag that DoS policy above the other WAN DoS policy so that it is matched first. Now that traffic will be exempted from inspection and anomaly blocking.