Advanced Data Blog
Our official blog with news, technology advice, and business culture.

9 Smart Ways for Small Businesses to Incorporate Generative AI
There is no escaping the relentless march of AI. Software companies are rapidly incorporating it into many business tools. This includes tools like Microsoft 365,

9 Smart Ways for Small Businesses to Incorporate Generative AI
There is no escaping the relentless march of AI. Software companies are rapidly incorporating it into many business tools. This includes tools like Microsoft 365,
7 Helpful Features Rolled Out in the Fall Windows 11 Update
In a world where technology constantly evolves, Microsoft stands at the forefront. It continues to pioneer innovations. Innovations that transform how we interact with our digital universe. The fall Windows 11 update is a testament to Microsoft’s commitment to excellence. It’s more than just an upgrade. It’s a leap into

Why You Need to Understand “Secure by Design” Cybersecurity Practices
Cybersecurity has become a critical foundation upon which many aspects of business rely. Whether you’re a large enterprise or small business, network security is a must. Cyberattacks can have long-term consequences. The frequency and sophistication of cyberattacks continue to increase. In 2022, IoT malware attacks saw a sobering 87% increase.

10 Biggest Cybersecurity Mistakes of Small Companies
Cybercriminals can launch very sophisticated attacks. But it’s often lax cybersecurity practices that enable most breaches. This is especially true when it comes to small and mid-sized businesses (SMBs). Small business owners often don’t prioritize cybersecurity measures. They may be just fully focused on growing the company. They think they
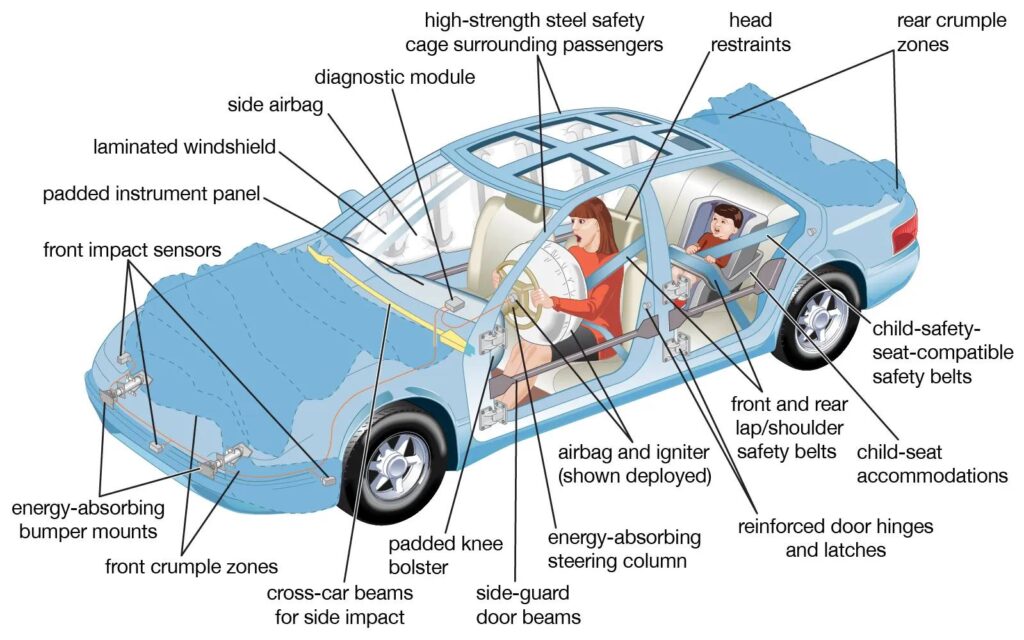
Why do I need to maintain a firewall subscription?
You might think it strange to start an article about firewall subscriptions by first talking about cars, but I promise this is perfectly relevant! If we went car shopping in the 1970s, today’s consumer would notice the vast difference of safety features in vehicles compared to modern standards. The car

Fortinet Security Advisory – Critical Authentication Bypass in FortiOS
Today Fortinet announced a critical authentication bypass in its FortiGate products that could lead to administrator access. This vulnerability, CVE-2022-40684, has been patched and admins are advised to upgrade or implement workaround safeguards immediately. The communications Fortinet sent to customers indicate that the newer FortiOS 7 releases are vulnerable and
Goodbye Antivirus, Hello EDR!
For as long as we can remember, having antivirus (AV) software installed and updated was an important aspect of a healthy cyber security posture. However as threats have evolved, the tools that thwart attacks must evolve, and this includes antivirus. Threats are no longer predictable or static in nature, and

Link Lock Phishing Protection
91% of cyber attacks begin with a phishing email. Phishing remains the most common and successful way for hackers to get their foot in the door before infecting an organization with malware. Often, those phishing emails contain counterfeit links that will lead a victim to a file or site that

Hackers targeting HR with direct deposit change requests
Phishing is a cybersecurity attack where the perpetrator pretends to be a trusted source through an email. The thief may masquerade as your bank or your favorite place to shop and try to trick you into entering your username and password into their fake sites. Phishing emails are typically sent

New zero-day threat – Log4j
On Friday, a vulnerability called “Log4j” that effects a large variety of consumer and business applications was revealed. This threat effects a tool that many closed and open-source applications use for logging purposes. This vulnerability is rated at 10, which is the highest rating on the severity scale.

Thoughts on the Cisco ENCOR 350-401 Exam
Recently I passed the Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR) exam. Wow what a mouthful! With the current generation of Cisco certs, the ENCOR exam is the first step in the CCNP certification path. Having gone through the old regimen of CCNP certs I found many differences
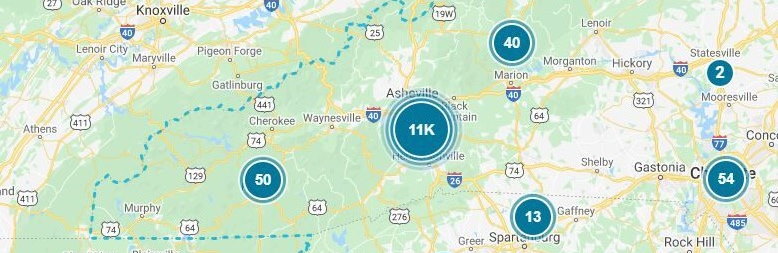
Recent regional and cloud outages
Within the past several weeks we’ve witnessed an unusually high number of outages that have impacted our clients in WNC. Some have been weather related and others due to system issues, but the end result is that businesses can’t reach their necessary services!

Thoughts on the Fortinet NSE7 SD-WAN certification
I just passed the Fortinet NSE7 SD-WAN certification! I prepared by using the self-paced training courses on the Fortinet Training Institute (FTI). As with all material currently on the FTI, the courses are prewritten scripts read by voiceover talent. This is as dry as training can get, especially when compared
