In my first post on showing the client IP addresses through a Barracuda ADC load balancer, I showed how to get Direct Server Return to work for clients on the same network by adding loopback interfaces on the back-end servers. In this post I will discuss a problem when using a layer 7 proxy service with Client Impersonation enabled on a multi-homed ADC.
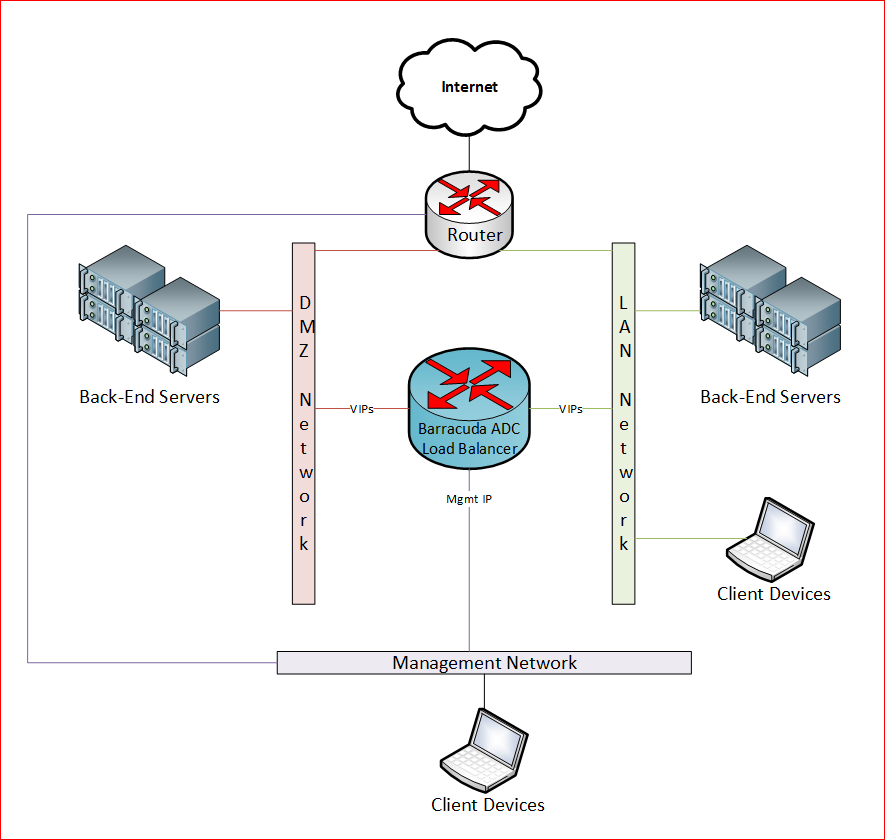
One of the requirements for client impersonation is that the back-end servers must use an ADC IP address as the default gateway. In traditional two-armed deployments where the real servers sit behind the ADC this is not a problem. However when the network is more complex and the ADC has interfaces in different networks and both VIPs and real servers sit on each of these networks then there can be some unexpected behaviors when it comes to the routing of packets.
For example this diagram shows an ADC that sits on a management network, DMZ and LAN. We have both VIPs and real servers on the DMZ and LAN.
The problem that occurs in this environment is that when back-end servers are setup to use the ADC as the default gateway, they can no longer get to other networks. For example, we discovered that packets that came from the back-end servers in the DMZ could not reach the LAN or get to the internet. We found that the packets were coming in on the ADC’s DMZ interface, but then leaving the ADC’s management interface! The Barracuda documentation states:
If you have multiple networks, you must specify a default gateway on the NETWORK > Routes page for every interface that accepts incoming traffic.
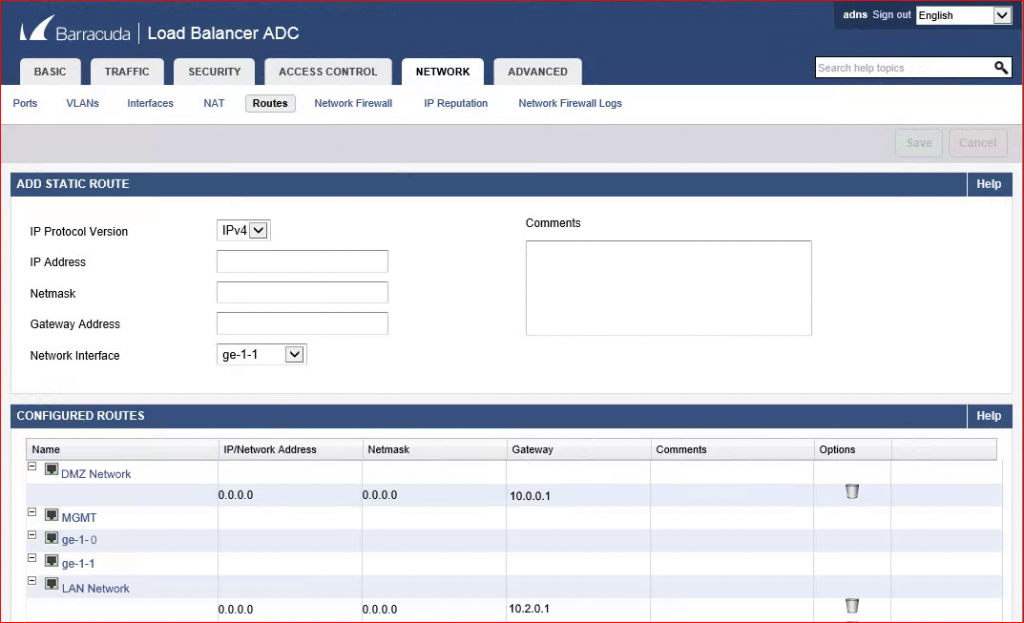
Even though default routes were added on the DMZ interface as shown below, the traffic originating from the back-end servers was not using the gateway for that network as specified.
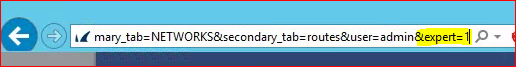
The solution is to first enable expert mode on the Barracuda ADC by adding “&expert=1” at the end of the ADC’s URL in the browser address bar. This will enable expert mode and reveal new menus and options.
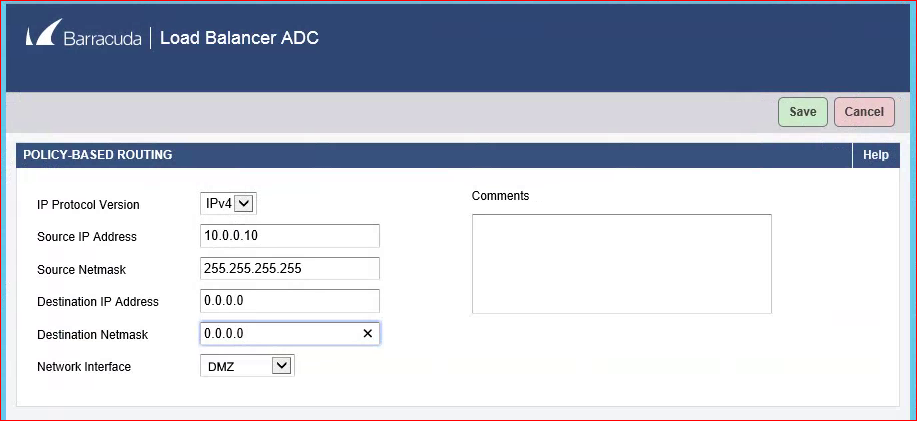
Go to Network -> Routes and there will now be a new section called Policy-Based Routing. Add a new policy-based route for each of the back-end servers. For example, for a real server with an IP address of 10.0.0.10: put 10.0.0.10 in the Source IP Address field, 255.255.255.255 in the Source Netmask field and 0.0.0.0 in both the destination IP and Netmask fields. Then choose the correct interface (DMZ in our example) and click save.
This will cause the ADC to match traffic coming from 10.0.0.10 and force it to use the DMZ interface for its next hop. Since there is a default route defined on that interface it will forward all the traffic to that router on the DMZ network.
Once we made this change, the backend server was able to reach other networks and the internet.
To learn more about using Direct Server Return on a layer 4 TCP service see the part 1 in this series.